top of page
Search


I am the Nth Generation – Jerry Craft
Learn more about Nth's most important asset – its people. What’s your job title? vCISO and Sr. Security Consultant How many years have...

Nth Generation
Jul 18, 2022


The Nth Files, Episode 5 - Cybersecurity insurance, and some of the challenges customers are facing
In recent months due to ongoing ransomware threats, our customers are finding it harder and harder to qualify for cybersecurity...

Nth Generation
Apr 13, 2022


The Nth Files, Episode 4 - Ransomware Readiness and Field Notes from the Experts ft. Derek Johnson
In this episode, Jerry Craft, vCISO and Sr. Security Consultant at Nth, and Derek Johnson, Sr. Cyber Security Engineer, GPEN at Nth,...

Nth Generation
Mar 2, 2022


The Nth Files, Episode 3 - Security Operations & Board Communications ft. Rich Lindberg
In this episode, Jerry Craft, vCISO and Sr. Security Consultant at Nth, and Rich Lindberg, contributing CISO, discuss how to build...

Nth Generation
Feb 18, 2022


The Nth Files, Episode 2 - Ransomware 2022: A Never-Ending Tail of Extortion and Crime
In this episode, Jerry Craft, vCISO and Sr. Security Consultant at Nth, covers the latest concerns about ransomware in 2022, and reveals...

Nth Generation
Feb 1, 2022
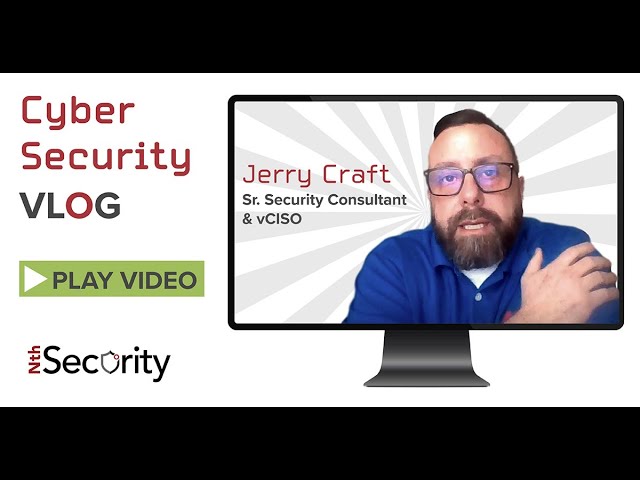

Nth Security Vlog Episode 1 - Post Incident Response: Log4j
By: Jerry Craft, Nth vCISO + Sr. Security Consultant As a tenured Sr. Security Consultant and vCISO at Nth Generation, I meet daily...

Nth Generation
Jan 12, 2022


Data Retention. Wait, what?
By: Jerry Craft, vCISO, Sr. Security Consultant | Nth Generation As a virtual CISO, I have the pleasure of meeting with many different...

Nth Generation
Dec 13, 2021


Matthew Broderick, BBS Systems, and Nth Huddle - What's it all about?
By: Jerry Craft, Nth vCISO and Senior Security Consultant Looking for a place to chat with experts? In the late ’80s and early ’90s, I...

Nth Generation
Nov 2, 2021


How long can I run my IT gear before it becomes a security risk?
IT organizations are used to running older servers, storage, and networking gear. The typical mantra is to run them as long as possible;...

Nth Generation
Jul 7, 2021


Encryption is so easy, that a caveman could do it!
I recently worked on a penetration test and discovered that a depreciated encryption method was being used. I often find this in MOST of...

Nth Generation
Jun 8, 2020
bottom of page



